Install openvpn server on Centos 7 Linux system

In this article we will discuss the installation of Openvpn server on Linux systems (RPM Family “Redhat 7/CentOS 7/Scientific Linux 7”).
VPN, or virtual private network, is a secure method of connecting remote internet resources together as if they were under the same LAN. OpenVPN is a tool for creating private networking tunnels between remote computers/servers that are not on the same local network. This is useful if you want to remotely access services on a network or computer without making those services publicly accessible.
Requirements:
- Linux server “any member of RPM Linux family”
- root access to the server.
Step 1: Installing OpenVPN Server
OpenVpn isn’t available in the default repositories. So we need to install Enterprise Linux (EPEL) repository. Run the following commands as a root to install the required repositories and OpenVPN server.
# yum -y install epel-release.noarch # yum -y install openvpn easy-rsa
Here’s we installed the openVPN server, and also installed easy-rsa which used for generating our SSL key pairs, which will secure our VPN connections.
Now we need to copy the openvpn.conf sample file into /etc/openvpn, so Run the following command:
# cp /usr/share/doc/openvpn-*/sample/sample-config-files/server.conf /etc/openvpn
Also, we need to create a directory for holding our generated keys and certificates using the below command:
# mkdir /etc/openvpn/rsa
Finally, copy the key and certificate generation scripts into the directory as below:
# cp -rf /usr/share/easy-rsa/2.0/* /etc/openvpn/rsa
At this point we are ready to Generate our keys,and certificates.
Step 2: Generating Keys and Certificates
Now, we’ll need to generate our keys and certificates. Let’s start step by step to generate the needed keys, and certificates.
Here you can specify the identification information for your OpenVPN server’s certificate authority, which then will be passed to client certificates. Changing these fields is optional and you can always input them manually during certificate creation, but setting them here creates less work during client cert creation. We use vim text editor to edit vars file
# vim /etc/openvpn/rsa/vars
Update the following entities with your openvpn server data:
. . . # These are the default values for fields # which will be placed in the certificate. # Don't leave any of these fields blank. export KEY_COUNTRY="EG" export KEY_PROVINCE="BH" export KEY_CITY="Kafr El Dawar" export KEY_ORG="MimasTech.com" export KEY_EMAIL="contact@mydomain.com" export KEY_OU="Systems Engineering" # X509 Subject Field export KEY_NAME="Mohammed Semari"
As I said before the above modifications are optional, but before we leave this file, there are two other important entities you may need to change their values:
One of the two important entities is the root CA key expire, the default one was 10 years I made it one year.
# In how many days should the root CA key expire? export CA_EXPIRE=365
Then come the client certificate expiration date, one year is good to have more control on you clients
# In how many days should certificates expire? export KEY_EXPIRE=365
Save and exit the vars file.
The following steps will generate the server root CA, server certificate ” optional “, and client certificate, So run all the below commands
# cd /etc/openvpn/rsa/ # source ./vars # ./clean-all # ./build-ca # ./build-key-server server # ./build-dh # ./build-key <client_name>
In the above commands, we sourced the changes we made in vars file, then cleaned previously existing keys and certifications which may exist in the keys directory, then create the root CA, then the server certificate” which is optional to add a more secure layer to the connection”, then generate Diffie-Hellman key exchange file “will take some time to complete”, finally create the client key and certificate.
Hints: 1. We need to press ENTER for each blanked field we asked to fill, also answer y in case of questions. 2. <client_name> is your client name, each client must has a unique/descriptive name for better control on them, and for security aspects.
We need to copy the generated files into our OpenVPN directory, Run the following commands:
# cd keys # cp dh2048.pem ca.crt server.crt server.key /etc/openvpn
Next, For client to connect to the openvpn server, He needs to have three files we generated previously ” ca.crt, client.crt, client.key”, Also he will need a configuration file for the client software he will use to connect to the openvpn server, this file we will create under name “client.ovpn”. This file contains the following entities:
client dev tun proto udp remote <openvpn server IP> 1194 resolv-retry infinite nobind persist-key persist-tun comp-lzo verb 3 ca ca.crt cert <client_name>.crt key <client_name>.key
Just replace the entities between < > with your server IP address, and client certificates, and Send the four files to your client.
At this point we are ready to configure the openVPN server.
Step 3: Configuring OpenVPN
Now it’s time to configure the openvpn server, the file is self-explanatory file, each fiel has explanation above it. I’ll go and do a minimal changes for the openvpn server to start.
Let’s edit the configuration file:
# vim /etc/openvpn/server.conf
We need to change the dh file name to be dh2048.pem. Because the default Diffie-Hellman encryption length we previously generated by Easy RSA was 2048 bytes. Find the entity and change it with . This is a mandatory step for the openvpn to work
dh dh2048.pem
Next comes the optional steps, we need to uncomment the push “redirect-gateway def1 bypass-dhcp” line, which tells the client to redirect all traffic through our OpenVPN.
push "redirect-gateway def1 bypass-dhcp"
Hints: 1. This step and the below 4 steps are optional. 2. Uncommenting the redirect-gateway means forcing clients traffic to go to the openvpn, your clients will be forced to follow your Firewall rules, and your internet usage policy. They may not be able to surf the internet while connecting to your openvpn. 3. For me I received many complains from clients about not able to use the internet while connecting to my openvpn, So I commented this entity again, Now they can connect to my Openvpn, and enjoy their normal use of the internet.
Next we need to provide DNS servers to the clients, this step is needed if you enabled the push “redirect-gateway def1 bypass-dhcp”, otherwise leave it commented
push "dhcp-option DNS 8.8.8.8" push "dhcp-option DNS 8.8.4.4"
Finally, change user and group to nobody, as mentioned in the configuration file, it’s important for the none-windows systems
user nobody group nobody
Save and exit the OpenVPN server configuration file.
Hints: 1. I only changed the necessary field "dh dh2048.pem", the other five steps I made is optional. 2. The configuration file has many important fields, you can use tcp protocol instead of the default udp protocol, you can change the listen port, you can change the listen IP, etc... 3. Other advanced configuration parameters depending on your needs, in this article I used the minimal configuration changes.
At this point we are ready to enable traffic routing to our openvpn.
Step 4: Traffic Routing
Now, we need to enable the IP forwarding on our openvpn server.
To enable IP forwarding in sysctl. Use the below command:
# echo "net.ipv4.ip_forward = 1" >> /etc/sysctl.conf
Now we need load this modification either you reboot your server “not preferred step” or run the below command to have the same effect of rebooting the server:
# sysctl -p
At this point we are ready to enable firewall rules on our openvpn server.
Step 5: Securing the Server
Securing your server against different types of attacks is one of the most important tasks systems engineer must master, we will discuss this topic in details in another article,but now will will secure our openvpn server using iptables, and firewalld.
If you did not enable either iptables or firewalld on your server, YOU CAN SKIP THIS STEP AND GO DIRECTLY TO THE NEXT STEP “STARTING OPENVPN”
THIS STEP IS OPTIONAL, BUT IT’S VERY IMPORTANT, let’s play with some iptables rules:
On RPM Linux Family “Redhat 7/CentOS 7/Scientific Linux 7” you can either use iptables or firewalld service
Case I: If you are using Iptables “As me”
Depending on the installation of your Linux server you may / may not need to install iptables service, Run the below commands to install and start it “IF IT’S NOT RUNNING AND YOU NEED TO RUN IT”:
# yum -y install iptables-services # systemctl enable iptables # systemctl start iptables # iptables --flush
You may not need to run the above steps if the iptables service is already running on your machine.
Next, We need to add two rules to iptables. Open port 1194 with protocol upd, and add a postrouting NAT Rule run the following commands:
# iptables -A INPUT -p udp -m state --state NEW -m udp --dport 1194 -j ACCEPT # iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
Then we need to save these two rules for permanent use, rum the following command:
# iptables-save > /etc/sysconfig/iptables
Case II: If you are using Firewalld
Again depending on the installation of your Linux server you may / may not need to install firewalld service, Run the below commands to install and start it “IF IT’S NOT RUNNING AND YOU NEED TO RUN IT”:
# yum -y install firewalld.noarch # systemctl enable firewalld # systemctl start firewalld
You may not need to run the above steps if the firewalld service is already running on your machine.
Next, We need to add openvpn service to existing firewalld services, and add masquerade also, run the following commands:
# firewall-cmd --permanent --add-service=openvpn # firewall-cmd --add-service=openvpn # firewall-cmd --permanent --add-masquerade # firewall-cmd --add-masquerade
At this Point the two cases of securing your RPM Linux Family “Redhat 7/CentOS 7/Scientific Linux 7” is completed, Again this section is optional.
Now, we are ready to start the openvpn server.
Step 6: Starting the OpenVPN server
Now, let’s go and enable then start the openVPN service. Run the following commands:
# systemctl enable openvpn@server # systemctl start openvpn@server
Let’s check that the service is already running, to do this we need to do three checks:
Check 1: SERVICE CHECK
This check shows to us if there are any configurations error in /etc/openvpn/server.conf configuration file, run the below command:
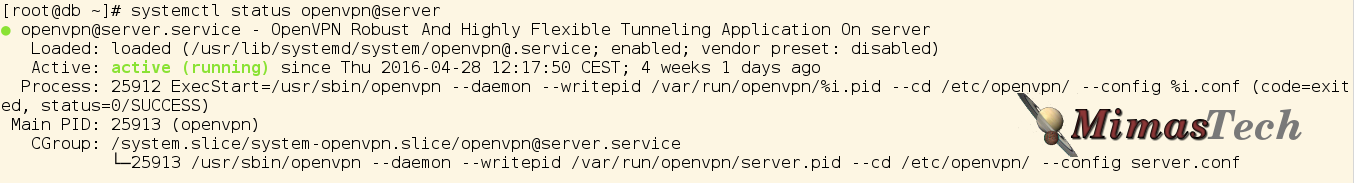
# systemctl status openvpn@server
This command output should be something like the below image
This image shows that the openvpn service is up, enabled, and running.
Check 2: NETSTAT CHECK
The above check ” service check” is not enough, we need to do another important check to make sure that the service is running, we need to run the next command:
# netstat -nlup
You will find port 1194 assigned to openvpn, as the below image
Check 3: IFCONFIG CHECK
The above two checks show that we successfully configured the openvpn service, but we need to do another check ” optional check ” to see the installed NIC interface that openvpn uses, we need to run the next check.
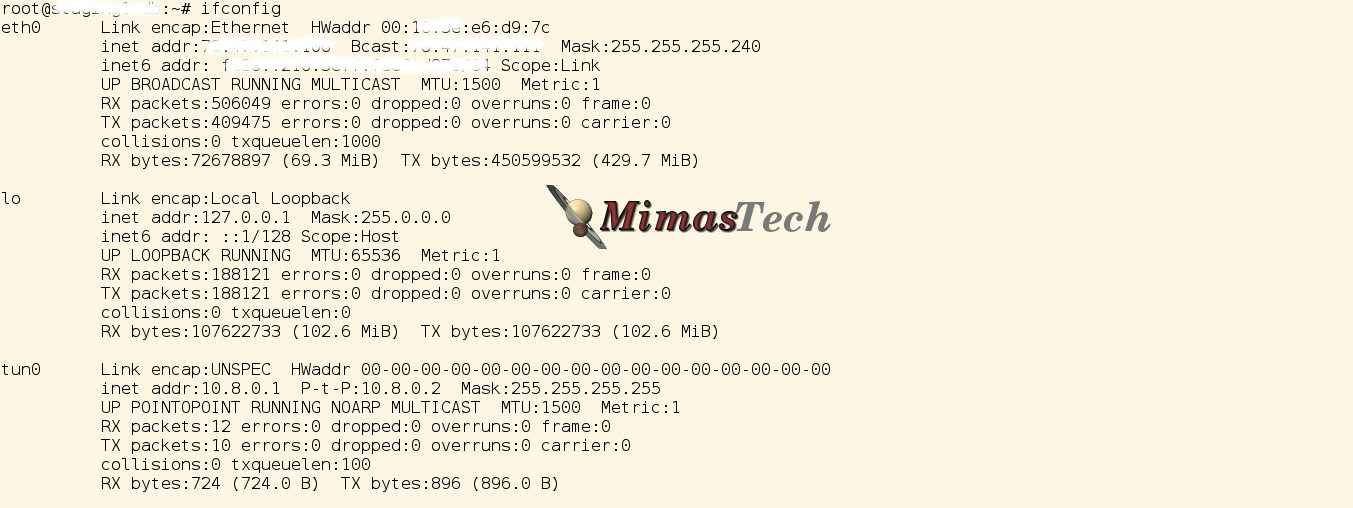
# ifconfig
You will find a new installed NIC interface with name “tun0” and configured to use this IP address “10.8.0.1” as the below image
At this point the server is running and well configured.
Notes: 1. Why should I run at least two checks to check that the openvpn service is running? Here's the answer: This because that the first check is only check on the configuration file, and it succeeded with me, but when I tried to connect to the server I couldn't, so I run the other two checks, and discovered the the service is already running, and well-configured, but netstat check didn't show that the openvpn service use port 1194, also ifconfig check didn't show any installed new NIC "tun0". I tried to figure out what is missing, sure there is nothing missing in the openvpn configuration file, so I searched deeply for the cause of this error, and discovered the reason. THERE IS A MISSING KERNEL MODULE I MUST INSTALL, I MUST INSTALL THIS KERNEL MODULE "tun" IT USED BY THE OS TO CREATE THE NIC INTERFACE USED BY OPENVPN, IF THIS MODULE IS MISSING THE SERVER WILL NOT COMPLAIN ABOUT ANY ISSUE IN THE CONFIGURATION. SO IN CASE OF CHECKS TWO AND THREE ARE NOT SUCCESSFUL YOU MUST GO AND CHECK ON THE EXISTENCE OF "tun kernel module" BY RUNNING THE BELOW COMMAND" # lsmod |grep tun This command shows the existence of this important module, if the above command didn't give any output then you are facing the same issue I faced before, then go and install this kernel module by running the following command: # modprobe tun Now we installed the missing module, we need to reboot our machine to test the success of the whole configuration, run the below command to reboot your system: # reboot When the system is up again , rerun the three check. they must give a positive outputs.
So we have successfully completed all the server-side configuration for OpenVPN. You need now to configure the clients machines to connect to the openvpn server, go and check our article for setting up a client connection to openvpn server using a different OSes “Windows, Linux, and Mac”.
Summary
In this article we have explained the installation, and configuration of the OpenVPN server, we completed our set-up in six steps, one of them is optional, but most important for a good Systems Engineer “Step 5: Securing the Server”. We also included the solution of an issue that faced us while testing the set-up of the openvpn server. Now you can safely protect you important services from being publicly accessible through the internet.
I hope this article is good enough for you.
See you in other articles.

If You Appreciate What We Do Here On Mimastech, You Should Consider:
- Stay Connected to: Facebook | Twitter | Google+
- Support us via PayPal Donation
- Subscribe to our email newsletters.
- Tell other sysadmins / friends about Us - Share and Like our posts and services
We are thankful for your never ending support.